Before the Breach
Too many companies ask: “I’ve been breached, now what?” It can happen to any organization. Suffering a data breach can be a catastrophic event, even for companies who *think* they’ve limited their exposure to a cyberattack. If you’re wondering what to do once you’ve experienced a cyber attack, you’ve already given cybercriminals too much of a head start. Find out some of the simple steps you can take to save you from a potentially business-ending event.
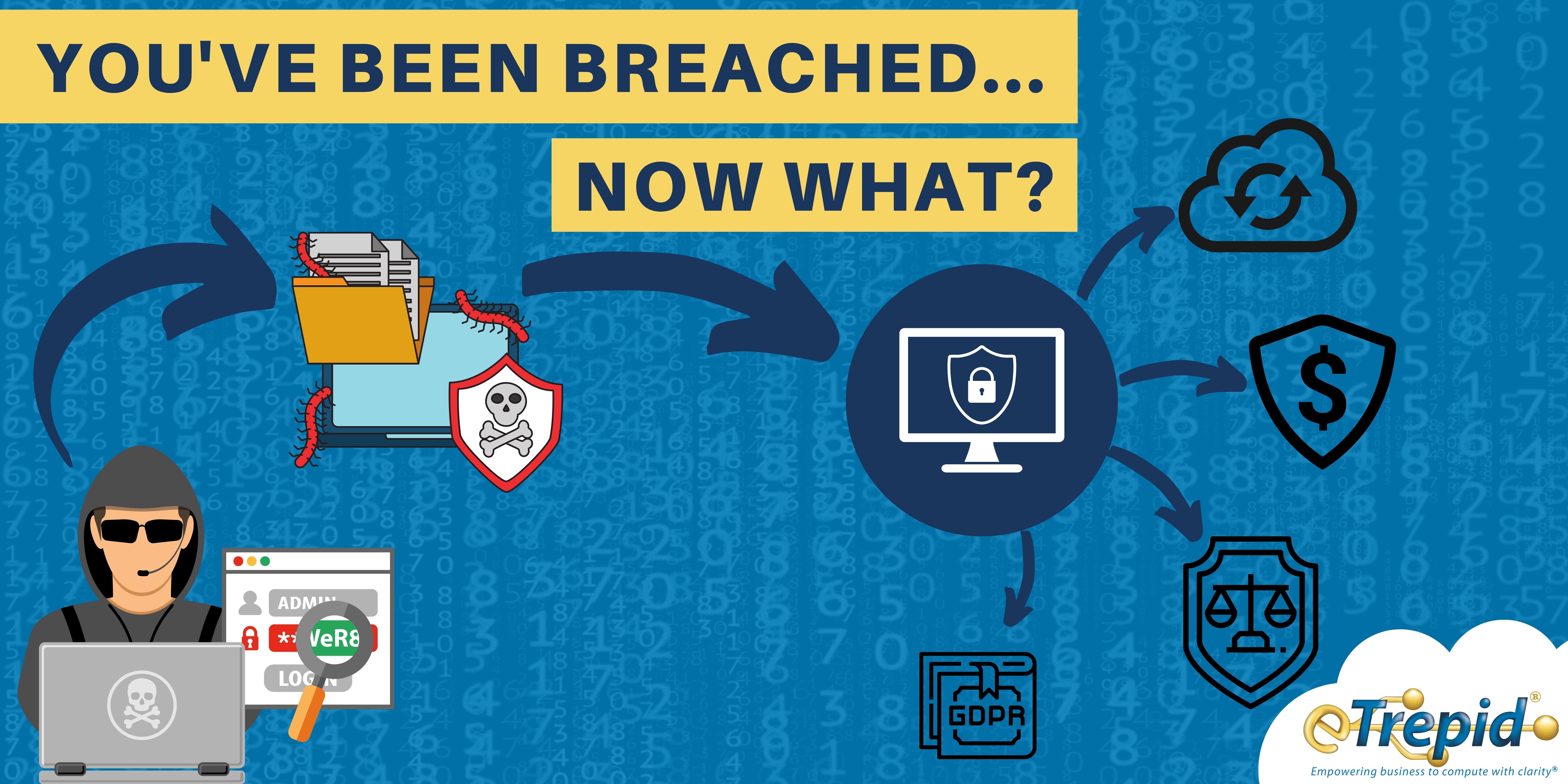
You've Been Breached… Now What?
If your company has fallen victim to a data breach in the past year, you're not alone. Even tech giants like Facebook, Amazon, and Twitter have suffered data breaches, despite dedicated teams of security experts and nearly limitless resources at their disposal.
Regardless of a company's size or revenue, the way it chooses to respond to a data breach has significant consequences, good or bad. Breaches often cause critical damage to businesses resulting in substantial financial losses that can bring major legal repercussions and ruin brand reputations.
Find out if the recent Facebook breach compromised your data
The best approach to responding to a data breach begins with preparation and strategic planning. Preventing breaches should be the goal of every cybersecurity plan overall, but motivated and innovative criminals make this a cat and mouse game. In fact, due to more than 3,000 publicly reported breaches last year, more than 46 billion confidential records were exposed, leading security experts to describe 2020 as "the worst year on record" for data breaches.
Make no mistake, if getting hacked is what finally gets you to focus on preventing an attack, you could be in trouble. By the time you've been hacked, you’re at the mercy of bad actors and expensive solutions with no guarantees about the road ahead.
Below, we'll look at some of the most effective incident response strategies and basic guidelines that businesses like yours can follow to prevent and recover from attacks and minimize the damage.
Cybersecurity Preplanning
It's worth repeating, planning your responses to potential breach scenarios is the first step in effectively responding to incidents. Identifying vulnerabilities in existing systems, establishing risk thresholds, and defining breach indicators allows team members to react to anomalies in your systems more rapidly. It’s no coincidence that companies with clear procedures and guidelines are able to respond to breach scenarios more quickly and with greater efficacy than those without.
Preplanning includes designating an Incident Response Team (IRT) that establishes clear roles and responsibilities for staff when responding to breaches. Team members should be trained on incident response procedures and conduct routine training exercises in implementing appropriate response plans.
Have a Backup Strategy
Having solid backups is essential for business continuity and critical for your cybersecurity playbook. We advocate heavily for never paying the ransomware as long as you can recover your data. Otherwise, reformatting your business computer systems and losing valuable data will be a harrowing experience. That's why you need a backup strategy, even if you reside in the cloud.
Prioritize Legal and Financial Protections
Companies responding to data breaches should not attempt to do so alone – legal counsel, insurance carriers, and security firms specializing in incident response can dramatically change the amount of time, effort, and money it will take to recover. Be sure you have clearly defined insurance coverage that provides cyber liability insurance and covers the various plausible incident scenarios established by preplanning.
Many insurance agencies even offer coaches to help guide clients through the recovery process. In the event of an incident, be sure to notify legal counsel experts in cyber incident management and applicable regulations as quickly as possible. Insurance carriers, attorneys, and business owners should maintain open communication about the incident, and the function of these support roles should be made clear to business owners throughout the process.
Engage a Reliable Cybersecurity Company
Companies without a contractual relationship with a cybersecurity company in advance of a breach often take three times longer to respond appropriately.
Believe it or not, even some managed service providers think of cybersecurity as an afterthought and something that they do after a cyber event happens. That's why it's imperative to work with a cybersecurity company that maintains strategic planning and prevention as part of its core playbook and offers that expertise to their customers.
Even robust, in-house security teams benefit from "surge" assistance early in the attack remediation efforts. Having an established relationship minimizes delays because forward-thinking firms bring a full range of cybersecurity services that help you both in the short and long term.
Know Notification Requirements and Law Compliance
In most jurisdictions, the law requires businesses that discover data breaches to notify affected consumers and clients within a specific time frame. As part of the pre planning process, companies should be educated on the notification time frames and compliance officers should establish guidelines for notifying compromised clients as quickly as possible. Failing to comply with notification laws can have severe legal repercussions for a company and permanently damage the company's reputation.
Read about the Amazon employee responsible for a recent data breach
Close up the Hole
Once breached, you need to understand where the unauthorized user has been to start building out a recovery plan and remediation strategy that not only removes the attacker from the network, but also closes up the point of entry.
Think Practically & Strategically
As long as there is money to be made from illegally obtaining and selling sensitive data, breaches will continue. These threat actors are groups of people who have unlimited time, unlimited resources, and they're going to keep poking until they find a way in.
As you can see, the best response to a data breach is preparing for one. At eTrepid, we advocate that you take an approach as if you are already compromised. Plan your cybersecurity policies around what happens when a breach does happen because, in the end, hackers will target your systems. If your cyber defenses aren't where they need to be, a breach is inevitable.
While it may not be possible to prevent these breaches completely, companies can significantly reduce the impact of incidents by methodically planning their responses before breaches occur.
Learn More About Breaches
Identifying risks, practicing scenarios, and securing external support ensures that businesses can efficiently and effectively recover. Rapidly notifying compromised clients allows them to act in their own best interests quickly. Having open communication with clients about incidents (and how you are responding to them) helps build and maintain trusting business relationships.
Consult with our cybersecurity experts about the individual risks you face so we can establish plans for your team to know what to do in the unfortunate event that your company is the next target.


.png)
Leave A Comment